![[SAT Homepage]](sat.gif)
![[SAT Homepage]](sat.gif) |
XSAT Project: Short Description |
| Object 1 | Object 2 | Object 3 | Object 4 | Object 5 | Object 6 | ... | |
| User1 | - | - | change | change | - | - | ... |
| User2 | - | - | - | - | read | - | ... |
| ... | ... | ... | ... | ... | ... | ... | ... |
| Group1 | change | change | - | - | change | - | ... |
| Group2 | read | read | exec | exec | - | read | ... |
| ... | ... | ... | ... | ... | ... | ... | ... |
| Computer1 | Computer2 | ... | |||||
The access matrix is a sparse matrix and is stored as a large set of lists with one dedicated list per object. It is therefore relatively easy to determine whether a user or group has access to a dedicated object. However, due to the effort involved, it is almost impossible to determine the set of objects any particular user has access to. This is a consequence, on the one hand, of the ease with which an administrator can inspect the non-empty entries of a column of the access matrix (=ACL); and, on the other hand, of the uselessness of standard tools in looking at a row of the access matrix.
Compounding the problem is the fact that a userís effective permissions are derived from multiple rows of the access matrix, since almost every user is a member of a number of (sometimes hierarchically organised) groups and collects permissions by group membership.
To make matters even worse, the access matrix itself is relatively large (in a standard system there exist hundreds of users and groups, and hundreds of thousands of objects such as files, directories, Registry keys, entries in the Active Directory, etc.). Since the objects are distributed amongst multiple computers, the access control information is also distributed. So it is much too time consuming and error prone to inspect all these objects without a special tool.
In addition, in most cases a user/group has access to a large set of objects, so even a simple listing of all objects that a user/group has access to is of no use. The listing would be far too long. Special effort must therefore be invested in order to ensure compact representation of this information.
The project will deal with "ad personam" permissions as well as effective permissions (which result from group membership) to ensure that the administrator need not rack his brain too much over group structure. In addition, the different concepts of inheritance (as stated above) shall be covered in the one approach.
The approaches developed will be evaluated in a test implementation based on Windows NT and Windows 2000. Special attention will be given to the NT file system (NTFS), the Registry, the Active Directory and the Metabase of the Internet Information Server (IIS).
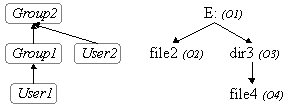 |
|
This - admittedly oversimplified and specific - example produces the following output when
asked about the effective permissions belonging to User1 on Computer1: E:\ [change].
The same query for User2 gives the following result: E:\ [read],
demonstrating that the user has read-access to the whole disk. The system then finds the exceptions to this - here given by the single extra line E:\dir3 [exec], which
shows that the user has only execute-access on this directory and beneath. (More detailed examples may be found in here.)