|
|
SAT General Overview |
This paper has been accepted for publication in the Journal of Network and Computer Applications
K. Hanner, R. Hörmanseder
Institute for Information Processing and Microprocessor Technology
(FIM), Johannes Kepler University, A-4040 Linz, Austria
One of the main tasks of an operating system is to share global resources among multiple users. Additionally, modern operating systems are able to control access to these resources in order to protect them against unauthorised user access. Windows NT makes use of access control lists (ACLs) to implement this feature. An ACL is a list of users and their permissions to access a specific object. It can be associated with any globally accessible object such as files, folders, registry keys, processes, pipe-endpoints and many others. However, the standard tools of Windows NT have limited functionality for managing these object permissions. For example, Windows NT only supports an object-centred view of these permissions. That means you can view and manipulate the permissions per object, but not per user. The subject of this paper is the realisation of a user-centred visualisation of object permissions. An application has been developed in the course of this project. It deploys several strategies for producing concise and clear representations of the permissions of a single user. An archive function maintains a history and you can therefore compare security settings from different times.
For example concerning a file C:\papers\SAT\v1001.doc within the NT file-system:
Every co-worker at the institute is a member of the group FIM-L. The members of this group FIM-L may read the file to discuss the contents. The authors of the document are allowed to change the document, and the group named Administrators has full access to the file.
So the ACL for the file is as follows:
| Group/User | Permissions | Comment |
| FIM-L | Read (RX) | staff of FIM |
| Hanner | Change (RWXD) | author of document |
| Hoermanseder | Change (RWXD) | author of document |
| Administrators | Full Control (All) | administrators |
We see that the ACL is closely in conjunction with the object. It is almost a part of the object itself. This leads to the following peculiarity in Windows NT:
Apart from some command-line tools (e.g. perms, xcacls, showacls) in the Windows NT Server Resource Kit [2], a huge set of tools exists for supporting NT administrators for managing file permissions. (See [3] for a list of some of them.) Many of these tools have impressive functionality. Nevertheless, most do not include a user centred view of permissions. Even if a user centred view is supported, the representation of the results has not fully satisfied us, because there often is no adequate summary of the presented output. Ultimately they produce a large amount of output.
Our intention is to consider these problems and to produce a concise yet meaningful visualisation of user permissions. We have not integrated any other functionality (e.g. modify permissions, analysis of user privileges or audit-information, ....), which is available in many other tools.
These considerations lead to the development of SAT (Security Analysis Tool).
One primary design requirement was that SAT should distinguish between two kinds of rights:
This chapter describes the principal design decisions for SAT. The current implementation only analyses files, whereas the underlying concept also is applicable e.g. for NT Registry [6] permissions.
The structure and co-operation of the components can be seen in Figure 1.
A considerable number of NT administrators worked on Novell 3.x before, and so did the authors. We were used to handling file-security based on the "runtime inheritance" of the Novell file-system and the trustees in Novell [7, p. 210ff and 244-246]. The step to "create-time inheritance" of permissions in NTFS [8, Concepts and Planning, Chapter 4, "how NTFS Permissions work"] leads to a change in the "philosophy of administration". So from our previous knowledge we lack some of the special features of Novell.
Unlike NT, Novell fileservers support a dual view of rights:
A partition into two autonomous components solves this problem:
This architecture has still more potential: The scanner stores any number of scans in one database, which means it makes "snapshots" of the security settings. In other words, it maintains a history of the security settings. So it is possible to compare scans of different dates with each other, without having to restore the data from a backup.
The SAT scanner is a highly distributed application, which consists of a Controller-module, a Master-module and any number of Slave-modules. You can classify the functionality of these parts as follows:
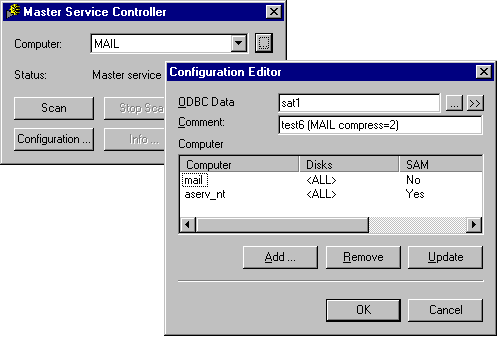
Figure 2: SAT Controller User-Interface
As mentioned before, the number of files can be (and will be, in most cases) extremely high. So clearly it is not enough to list all the files a user has access to. SAT filters the information and shows only security relevant details, particularly changes of security within the directory hierarchy. Furthermore, SAT is able to combine files with the same security settings. Five levels of compression define how files will be grouped together. The scanner of the SAT application includes most of these compression facilities, thus reducing the size of the database as well.
These compression levels imply loss of information. It is up to the user to find a tradeoff. Either he gets detailed information or a concise overview. Obviously a significant overview is more valuable for the administrator because, if the necessity arises to have a look at the full details, everything (except an overview) can be found via the standard tools of Windows NT.
Because of create-time inheritance used in NTFS ([1, p. 208]), every file has an ACL of its own. After creation of the file, its security is independent of changes in directory-permissions. Therefore during the lifetime of a disk-volume, changes of the security and file-moves lead to a set of files, which do not comply with the actual inheritance structure of permissions. The size of this set depends on different security needs as well as the quality of the predefined NTFS security structure and the strictness of the administration.
Novell experts will notice that their system does not have these compression and overview problems, because the file security information is already stored as Trustees in compressed form within the file-system (Keywords: Trustees, run time inheritance, Bindary [7]). In Novell, special rights for single files are assigned only as an exception.
SAT supports five levels of compression within the analysing slave component:
| level | name | short description | sample output |
| 0 | minimum | displayed including full filenames (This level uses a lot of space in the database and should therefore be used only on selected and small volumes!) |
|
| 1 | low | grouped together only if they all have same permissions |
|
| 2 | medium | same permissions are grouped together |
|
| 3 | high | are grouped together |
|
| 4 | maximum | - |
The following examples are based on compression level 2, which is a good choice for user-volumes.
The Viewer shows all data that has been collected in the security scan.
FIM\Hanner, Effective rights, Full Security Image
C:\papers\SAT [RWXD--] [RWXD--]
C:\papers\SAT\2 *.doc [RXWD--]
C:\papers\SAT\1 *.bmp [RWXD--]
C:\papers\SAT\1 *.bmp [R-X---]
C:\papers\SAT\2 *.txt [RWXD--]
Because all files in the example directory inherit an ACL stating that user Hanner has Change(RWXD) permissions on every file in the directory, only the exceptions to this rule are displayed:
FIM\Hanner, Effective rights, Only Changes
C:\papers\SAT [RWXD--] [RWXD--]
C:\papers\SAT\1 *.bmp [R-X---]
In some situations, all or almost all files or subdirectories change their permissions. Assuming there is a collection of private user-directories within a main directory named USERS. All users have List-Permissions(RX)() in USERS (probably) through a group. One level below in the directory hierarchy only the user himself has permissions on his personal directory.
So compression level "Only changes" leads to a long list of exceptions when looking at \USERS, because almost every user-directory is included with "no permissions" in the listing.
FIM\Hoermanseder, Effective rights, Only Changes
I:\users [R-X---] [------]
I:\1 *.ckm [R-X---]
I:\Administrator [------] [------]
I:\divUser [------] [------]
.................
I:\users\hanner [R-X---] [R-X---]
I:\users\hoermanseder [RWXD--] [RWXD--]
I:\users\muehlbacher [------] [------]
.................
When level "Only Changes + Optimisation" is selected, the Viewer detects that the inheritance of List-rights from \USERS to its subdirectories makes the listing longer. Therefore the Viewer displays these rights in small letters, indicating that these rights are not inherited. So from this point the assumption is that user Hoermanseder has no permissions in all subdirectories and files of \USERS. The Viewer only has to show the changes to this assumption. The listing only has to include two directories, because only the directory Hoermanseder as personal user directory and the directory of user Hanner are not compatible with this assumption.
FIM\Hoermanseder, Effective rights, Only Changes + Optimisation
I:\users [r-x---] [------]
I:\1 *.ckm [R-X---]
I:\users\hanner [R-X---] [R-X---]
I:\users\hoermanseder [RWXD--] [RWXD--]
Both the SAT scanner and viewer use Microsoft Open Database Connectivity (ODBC) for communication with the database. This makes the usage independent from the underlying database system. One is free to use a low cost solution (e. g. Microsoft Access) or a high performance database server such as SQL Server or Oracle.
The distributed modules of the SAT scanner communicate with each other via Remote Procedure Calls (RPCs). It is therefore easy to support any network protocol.
The Master- and Slave-modules are implemented as Windows NT services. A service is a background process running in a certain user context. This leads to the following conclusions:
Very often a scan covers only a part of the computers from a set of domains. SAT takes this fact into consideration. If a domain database (e.g. from a trusted domain) is not scanned, the Viewer nevertheless correctly displays all names of groups (and users) which are assigned permissions on the scanned NTFS-volumes. Obviously the relationship of users and groups of a domain is only included in the output, if the domain-database has been analysed.
In this section we try to give some screenshots to show how the Viewer works. For clarification, all of the following screendumps correspond to previous examples. To simplify matters, each example only presents a small section of a full output.
Figure 3 shows the effective rights of the user FIM\hanner on disk C: of the computer Mail.
Due to compression level 1 of the scanner, files with the same extension are only grouped together if they also have the same rights.
This is very convenient if one wants a detailed view on a small set of exceptions.
Because of the full display of the security image, all files and directories the user Hanner has access to will be displayed. This sample corresponds to the first description of ACLs in chapter 1 (Introduction) and to the description of compression level 1 in chapter 4.1 (Compression within the slave component).
The security of the file old_03.bmp has been changed specifically for this sample to show the functionality of compression level 1, so please do not ponder on the reason for this security-setting.
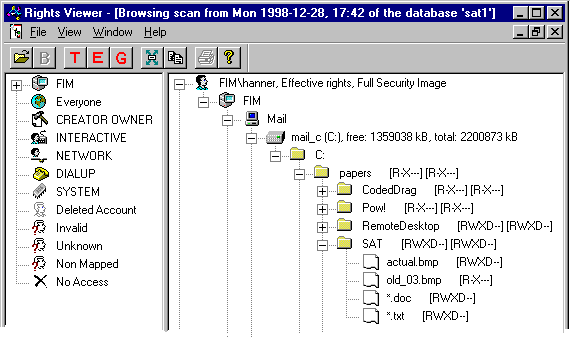
Figure 3: Effective rights of user FIM\hanner on disk C, level of compression = 1
On the left side of the Viewer in Figure 3 there is the list of all domains analysed (only FIM in this example) and the special groups and accounts (Everyone, CreatorOwner, Interactive, Network, Dialup, System [9, p. 45]), which may also be assigned permissions. The other accounts document special errors like rights assigned to an already deleted account. Directories which could not be analysed by the scanner due to insufficient rights are summarised under the account "No Access". This has been mentioned already in chapter 5 (Implementation characteristics).
Figure 4 shows the rights of the same user on the same disk with the compression option "Only Changes" turned on. As you can see, the number of files listed is less than the output before, due to the fact that only exceptions are displayed. This functionality has already been discussed in chapter 4.2 (Compression within the SAT Viewer).
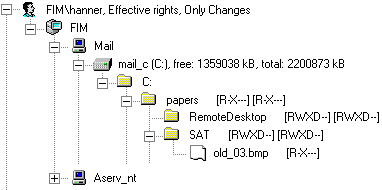
Figure 4: Show only changes in NTFS security
This example has already been presented in section 4.2.3. As a result of using compression level 3,
file-extensions are omitted. Figure 5 shows that user Hoermanseder not only has change(RWXD)-permissions in his personal home-directory, but also has Read(RX)-permissions in the home-directory of user Hanner. Additionally it can be seen that the user is also allowed to read the directory InetPub and all files/directories beneath.
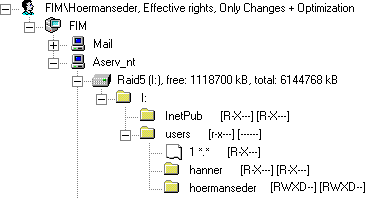
Figure 5: Effective rights, compression level 3 and optimisation of the presented overview
The optimisation recognises that it does not make sense to assume that user Hoermanseder has Read(RX)-permissions for all subdirectories in I:\USERS, because there are many other user-directories. User Hoermanseder does not have permissions for these directories. So the viewer shows that the user has permissions to read the directory, but has none beneath this level. Those permissions which are not inherited are displayed in small letters. Consequently, every file and directory beneath I:\USERS which can be accessed by user Hoermanseder is reported explicitly.
The SAT-Viewer has builtin functionality to export the data to the clipboard. Because this information is in pure ASCII-format, data can be used in any wordprocessor starting from Notepad or WordPad. The output is almost the same as shown in the compression examples
(chapter 4).
The following output corresponds exactly to the situation shown in the previous section 6.3.
Account: FIM\Hoermanseder
Kind of Rights: Effective rights
Compression: Only Changes + Optimization
Domain: FIM
Computer: \\Aserv_nt\I$
[R-X---] [R-X---] I:\InetPub
[r-x---] [------] I:\users
[R-X---] I:\users\1 *.*
[R-X---] [R-X---] I:\users\hanner
[RWXD--] [RWXD--] I:\users\hoermanseder
We analysed a set of three domain-controllers (Server for routing and RAS with about 300 MB of allocated file-space, mail-server with Exchange and 850 MB files and a file-server with about 13 GB of files). These three servers hold a total of more than 240,000 files in 19,500 directories. The number of users and groups is about 90 and therefore quite small.
The resulting size of the MS-Access database is less than 15 MB when selecting compression mode 2 (medium). Due to the size of the file-server, the total scan lasts about one and a half hours.
At the moment, the SAT application has, of course, some limitations and shortcomings. In addition to fixing some known bugs, we want to integrate remote installation functionality and make improvements of the analysis by using the concept of "dynamic ACL inheritance", which is available in NT 2000 and NT 4 with Security Configuration Editor [3] installed. The documentation of SAT is also somewhat poor at the moment.
Our long-term goal is to support an automatic comparison of successive scans and mark security-relevant differences between them.
The developed SAT application has not yet been released, because we see it as a prototype. Nevertheless, those interested in this topic should contact us to get a test version. Unfortunately, due to lack of personal resources, we can only support a small number of users.
References
References included here are only examples. A variety of books and course material cover these topics.
Kurt Hanner
(hanner at fim.uni-linz.ac.at) did his diploma thesis at the Institute for Information Processing and Microprocessor Technology and received his MSc from the University of Linz 1998. He worked with McAfee and NAI. At present he is serving in the Austrian army.
Rudolf Hörmanseder (hoermanseder at fim.uni-linz.ac.at) received his MSc from the University of Linz 1983. In 1983 he joined the "Forschungsinstitut für Mikroprozessortechnik". Since 1997 he has been a member of the Institute for Information Processing and Microprocessor Technology (FIM). His fields of interest are operating systems and system-administration.