This is a exemplary web server in Java which can be used as an educational tool for the demonstration and explanations of the most typical web security vulnerabilities, why they happen, how to exploit them, and how to prevent such security problems when programming in Java. This is the reason why this webserver is deliberately very vulnerable.
Because use of the Internet is rapidly increasing, security in this net becomes more and more important. The online shops, companies, or business are working online with big amounts of money and sensitive user's data and all of this should be stored in a safe place. Now most of the security problems are located in the application layer and are usually due to a faulty programing code. In this server, as we said above, we are using the Java programming language, but (almost) all attacks apply to (almost) all other programming language as well.
During the development of this exercise we will cover the most important security vulnerabilities, following the last OWASP guide, published in 2010.
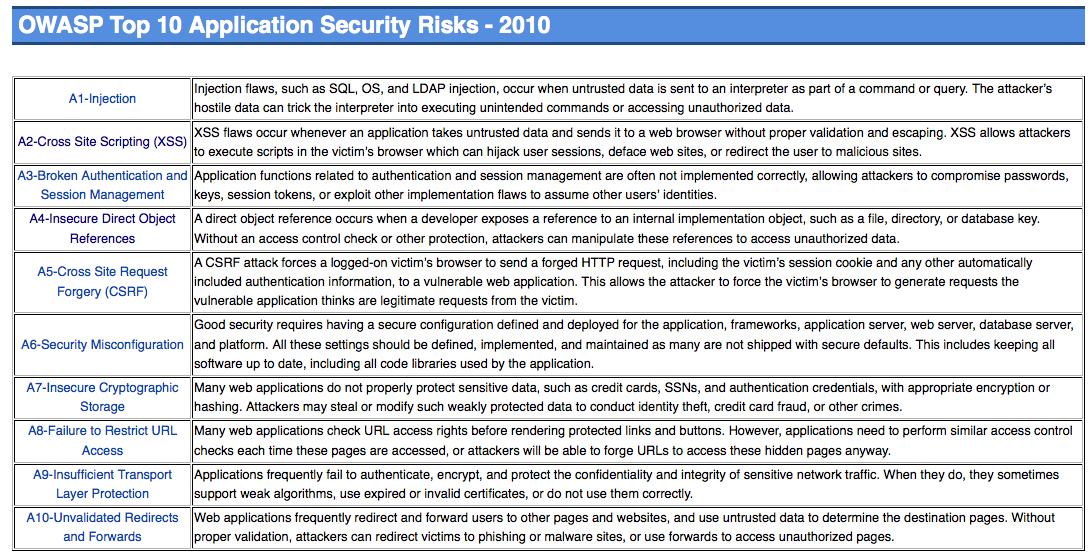
OWASP, stands for Open Web Application Security Project. It is an organisation that tries to fight against the causes which makes software insecure. You can look for more information about them under the link .
In order to cover most important aspects, we will show some more application not directly applicable to Java or easy to demonstrate to complete the web security topic.
The student can have different workflows in this webserver depending on the knowledge level. If the student has already some knowledge about web security and the possible attacks a web site can suffer, then he/she could try to attack each application without the previous introduction. For this aim there is a link to each vulnerable application in the top frame, "Direct access to the vulnerable application". In the top frame there is also available all the users passwords, which might be required for the individual applications.
Beginners should use the left frame, in which they can follow the normal webserver workflow by reading the introductory explanation to understand the flaw and risk, and then trying by themselves the mentioned application.
This is the current list of applications within the server. In the left side of the web page there is a short link to each of these applications.
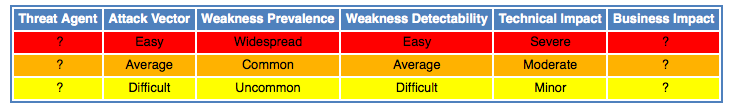
For all vulnerabilities we will include - as far as possible - a small summary about how common the weakness is, how easy the attack is and so on. You can find the possible values in the image below:
For each application we have the following deployment in the web server:
After the explanation of the main idea of this tool, I hope you will enjoy the experience!
Virginia Diaz Brugos